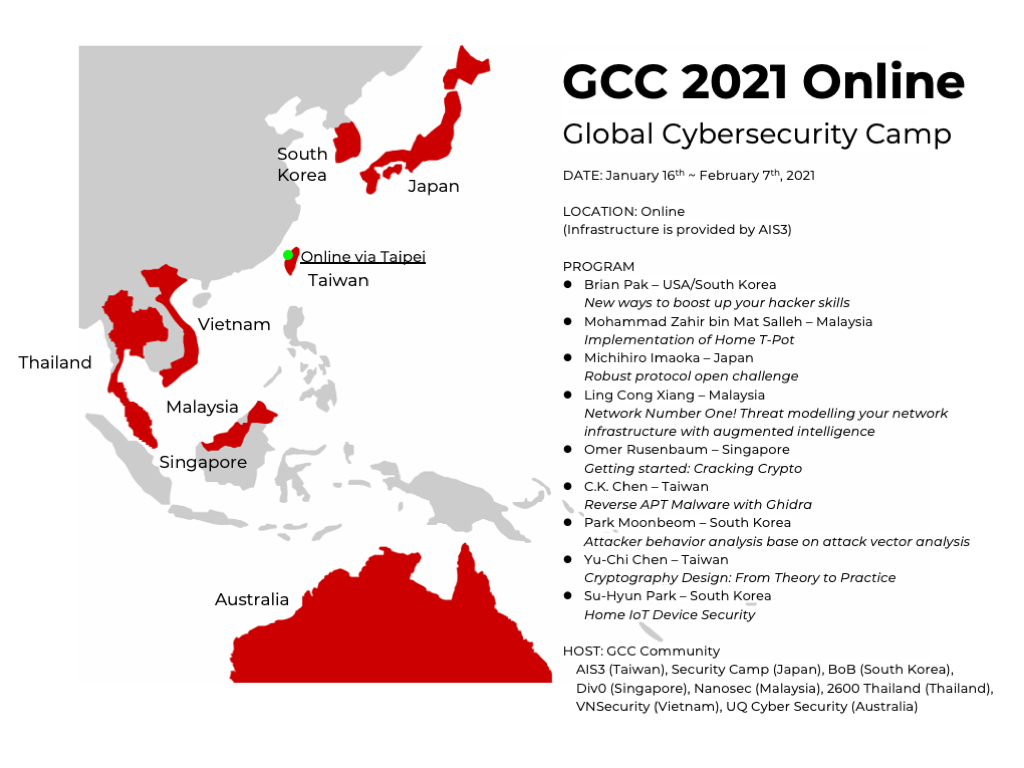
GCC 2021 Online
Introduction
- Location: Online (Infrastructure is provided by AIS3)
- Days: 16th January ~ 7th February ,2020
Every Saturday and/or Sunday during 9:00 AM to 6:00 PM (UTC+8) - Eight countries are participating (maximum 48 students)
- Pre-assignment of course will be held at Slack workspace
Mission of the GCC
Strengthen the security community across Asia and nurture future global leaders.
Annually, the best 48 students (maximum) from member countries gather in one of the participating countries for a week to exchange experience, forge a life-long friendship, and learn from the best cybersecurity professionals.
Non-commercial education programs and communities organize the program supported by industry leaders who care about the safe digitalization of the world.
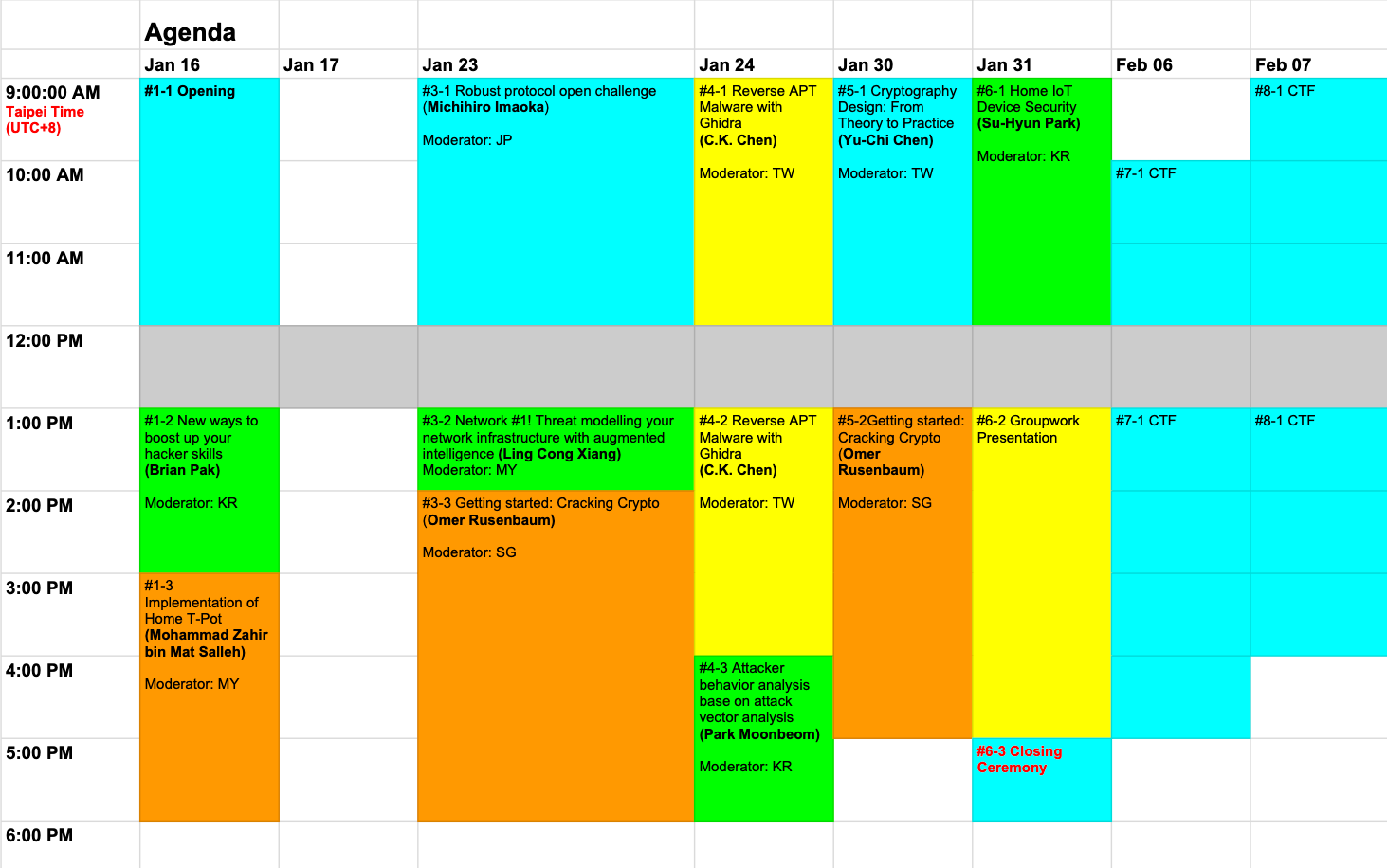
Timetable of GCC 2021 Online
Information of each lecture
New ways to boost up your hacker skills
Abstract
Recently, there has been a lot of interest in cybersecurity due to small and large incidents, but cybersecurity is still unfamiliar to most people. While cybersecurity is a field that has become essential for our safe digital life, there are not many convenient ways to learn the basics of cybersecurity and especially the in-depth knowledge, unlike other areas of education.
We have created a new space to study the concepts, practice with various exercises, compete through periodic CTFs, and ask questions/share knowledge. This education platform is designed for all skill levels: A student who just started studying to become an awesome hacker, a developer who wants to build safer services, and security experts who want to further sharpen their skills.
Introducing Dreamhack, the hackers’ playground.
We also harness the PatchDay, a bug bounty platform, with Dreamhack to ensure the learners successfully transition to real-world hackers.
Trainer
Name: Brian Pak
Bio :
- Graduated BS + MS from Carnegie Mellon University
- Founded PPP
- 5 time DEFCON winner (incl. 60+ international CTF wins)
- CEO of Theori
Implementation of Home T-Pot
Abstract
T-Pot is based on a vanilla Ubuntu 14.04.02 ISO image. The honeypot daemons as well as other support components we used have been paravirtualized using docker. This allowed us to run multiple honeypot daemons on the same network interface without problems make the entire system very low maintenance.
The encapsulation of the honeypot daemons in docker provides a good isolation of the runtime environments and easy update mechanisms.
In T-Pot we combine existing honeypots (glastopf, kippo, honeytrap and dionaea) with the network IDS/IPS suricata, the data monitoring and visualization triple elasticsearch-logstash-kibana, and our own data submission ewsposter which now also supports hpfeeds honeypot data sharing.
Trainer
Name: Mohammad Zahir bin Mat Salleh
Bio :
Mohammad Zahir acquired his Master’s degree in Computer Networking at Technology MARA University (UiTM Shah Alam) in 2014 and currently doing his PhD in IT at UniKL MIIT.
In 2009, Mohammad Zahir finished his studies at Kuala Lumpur University and acquired the Degree of Network System.
Mohammad Zahir has accumulated 11 years of experience in real working environment by applying all Information Technology (IT) knowledge such as Network and ICT Security.
Starting from Apprentice in 2009 at MIMOS Berhad under Network Team and then upgrade to Junior System Engineer at AIG Global Services also attach under NOC (Global Network Operation Center)
From 2010, he worked as Network Engineer in one of Malaysia Public University for nearly eight years (IIUM or UIAM). During eight years at University, he is also experienced in supervision of large-scale Higher Education sector in terms of planning and managing daily network, wireless and ICT security operations.
Resigned from Government staff and then coming back into Private Sector. Join one of top Facilities Management company in Malaysia which is GFM Services Berhad as a IT Engineer. Leverage all my experienced in ICT at this company to build up Data Center and best ICT infrastructure to support the clients. Involved in digitalization from manual process to computerized system.
Then, he jumps to one of top Banking Institution is Malaysia which is Maybank and in charge on WAN operation.
Mohammad Zahir now holds the position of Cyber Security Solution and Engineering at one of Telco company in Malaysia under Cyber Security Operation at CISO.
Robust protocol open challenge
Abstract
In general, cyber security tends to focus on protecting systems and data from attackers. In addition to this, securing communication from accidents and natural disasters is also considered to be an important element of cyber security. In this lecture, we will prepare a LAN (10BASE-T) that causes physical communication failure remotely. Participants will design and implement a robust protocol that enables communication in these faulty LANs, and compete for protocol resilience on various evaluation axes with a remote actual device.
Trainer
Name: Michihiro Imaoka
Bio :
Hiro Imaoka is a founder of Imaoca Engineering Office. He is also an FPGA developer, an embedded system developer, and a writer. He has been a Microsoft MVP since 2014 (Windows development), Security Camp lecturer since 2015, Security Camp producer since 2018, and a Sechack365 Trainer since 2020.
Network Number One! Threat modelling your network infrastructure with augmented intelligence
Abstract
A computer network is the fundamental piece of any infrastructure, offering medium for machines to communicate with one another. A network can be very simple, with a few subnets and routing rules, but in the case of corporate network, it often grows very complex, yet still works at the same time. As complex as it grows, we still want to know how subnets connect, and how threats slumber within the depths of complexity.
Trainer
Name: Ling Cong Xiang
Bio :
CTF Hobbyist, Developer, Security Engineer
Getting Started: Cracking Crypto
Abstract
Encryption and passwords a cornerstone of ours digital life this days. Although we feel safe, knowing our data is safe and secured under passwords and ciphers protection, there are ways to crack them and bypass security mechanisms. In this course, we will cover several ways to crack and bypass security. Participants will learn about:
- What is cryptography
- Hashes
- Bruteforce attack
- Dictionary attack
- Lookup table
- Caesar cipher and how to crack it
- Transposition cipher and how to crack it
- Substitution cipher and how to crack it
- Bypassing 2FA and Security Questions
Participants will have to write thier to solve some of the challenges in the course.
Trainer
Name: Omer Rusenbaum
Bio :
Omer is a Co-Founder and the CTO of swimm, a new startup helping vendors to ramp-up to new codebases with ease and speed.
Omer is an honorable instructor of DART Consulting and Training and trained several times in Singapore.
In his past, he served in the Israeli intelligence corps cyber units in R&D roles and was a keystone player in many trainings including managing the Checkpoint Cyber Academy.
On his spare time he is a coffee enthusiasts and explorer.
Reverse APT Malware with Ghidra
Abstract
In this course, we first introduce APT basic knowledge to realize the threat/behavior of the APT. Then we explain 3 different APT cases in Taiwan, Japan and Korea. For Taiwan’s case, Operation ShadowHammer is classical supply chain attack. JPCERT discovered the Taidoor malware is used in Operation Bitter Biscuit. Kimsuky, is the other state-sponsored APT compaign, targets many South Korean organizations.
To analysis these APTs, we then introduce the tools could be used for threat hunting, regularly tracking for hidden APT activities. The introduced tools include Moloch, ELK, Yara.
In the last part, we move to reverse the APT malware. Using Ghidra, we could analysis these APT malware. The technique to deal with APT samples are introduced here, e.g. PE Header, Decryption/Decoding, Shellcode, Data Structure and Import Table Hash.
Trainer
Name: C.K. Chen
Bio :
Chung-Kuan Chen is currently a senior researcher in CyCraft, and responses for organizing research team. He earned his PHD degree of Computer Science and Engineering from National Chiao-Tung University (NCTU). His research focuses on cyber attack and defense, machine learning, software vulnerability, malware and program analysis. He tries to utilize machine learning to assist malware analysis and threat hunting, and build automatic attack and defense systems. He has published several academic journal and conference papers, and has involved in many large research projects from digital forensic, incident response to malware analysis. He also dedicates to security education. Founding of NCTU hacker research clubs, he trained students to participate world-class security contests, and has experience of participating DEFCON CTF (2016 in HITCON Team and 2018 as coach in BFS team). He organized BambooFox Team to join some bug bounty projects and discover some CVEs in COTS software and several vulnerabilities in campus websites. Besides, he has presented technical presentations in technique conferences, such as BlackHat, HITCON, HITB, RootCon, CodeBlue OpenTalk, FIRST and VXCON. As an active member in Taiwan security community, he is in the chairman of HITCON review committee, and ex-chief of CHROOT - the top private hacker group in Taiwan.
Attacker behavior analysis base on attack vector analysis
Abstract
Analysis hacking technique to analyze the victim system hacked by the attacker, and analysis various artifact on the victim system to reconstruct the attacker’s behavior.
Outline
- Attack techniques and vector to hack to server system
- Types of artifact and log analysis techniques
- Analysis the types of artifact according to each attack technique
- Reconstruct attacker’s behavior base on evidences(Artifact)
Trainer
Name: Park Moonbeom
Bio :
I’m working in cyber security and incident response sector of South Korea as a general researcher and cyber investigation advisory member of the national investigation agency. Also I’m responsible for research on hacking methods, analyze hacking incident also, profiling the relationships. And I’m not only one of the leaders in Asia’s oldest underground hacker group, but also an instructor and mentor in the program(a.k.a BoB) to train ethical hackers in South Korea.
Cryptography Design: From Theory to Practice
Abstract
Cryptography is the science of designing algorithms and protocols that can guarantee privacy, authenticity, and integrity of data when parties are communicating or computing in an insecure environment. The recent explosion of electronic communication and commerce has expanded the significance of cryptography far beyond its historical military role into all of our daily lives. In particular, cryptography provides the technology for realizing different kinds of security; for example, it allows us to use our credit card to make online purchases without revealing the credit card number to other people. The past 25 years have also seen cryptography transformed from an ad hoc collection of mysterious tricks into a rigorous science based on firm complexity-theoretic foundations. In this talk, we start by introducing basic mathematical tools and well-known and practical cryptosystems (including AES, RSA, and ElGamal). Then, we move theoretical aspects to discuss how to convince everyone of the security. Finally, we will describe secret sharing and its potential applications. The projects include secret sharing implementation and a few crypto-style CTF.
Trainer
Name: Yu-Chi Chen
Bio :
Yu-Chi Chen is currently an Associate Professor with the Department of Computer Science and Engineering, Yuan Ze University, Taiwan. His research interests include cryptography, information security and blockchain.
Home IoT Device Security
Abstract
There are a lot of home IoT (Internet of Things) devices at your home these days. Smartphones, tablets and smartwatches are very common. Smart TVs, fridges and even door locks and multiplugs are now connected to the Internet nowadays. I will discuss how securely these devices are communicating through the web.
Outline
- Network basics
- Wireshark and traffic captures (hands-on training)
- How IoT devices works
- Raspberry Pi and WiFi AP
- How you can secure these devices
Trainer
Name: Su-Hyun Park
Bio :
LinkedIn
Senior software engineer on embedded arena, from small IoT device to large scale network security appliance, UTM.
Started programming since mid-80’s (since 8 years old) on XT-PC, pre MS-DOS generation.
Have experienced more than 20 programming languages over 30 years, but now I am a linux systems software engineer developing on kernel module and user space applications especially on embedded systems.
On the other hand, I am a full-stack engineer. Developing from Android app to the back-end server applications for hobby project.
Familiar with a lot of high-tech ICT technology such as IoT, AWS cloud architecture, Web services as well as App services applications. Also have experienced with computer vision applications using OpenCV and Tensorflow, CNN network for AI/ML image processing.
Likes to solve challenging problems and enjoy self-studying and learning. Willing to relocated anywhere in the world as long as there is interesting job and position. :wink:
- Certifications : P.E., KCISA, CISSP, CCDP, CCNP, CCDA, CCNA, ITILv3 certified
- Industry domain : Network, Security, Firewall, UTM, IoT, Embedded
- Core technology : Linux, Kernel, Netfilter, Packet processing, Communications
- Development platform : Linux, Windows, Android, AWS (Amazon), GCP (Google), Yocto, Buildroot, Crosstool
- Programming Languages : C, C++, Java, Kotlin, Python, Go, HTML, JavaScript and more
- Library : OpenCV, Tensorflow
- Hobby Programming : Web Crawling, AI (Maching Learning), FinTech, Blockchain