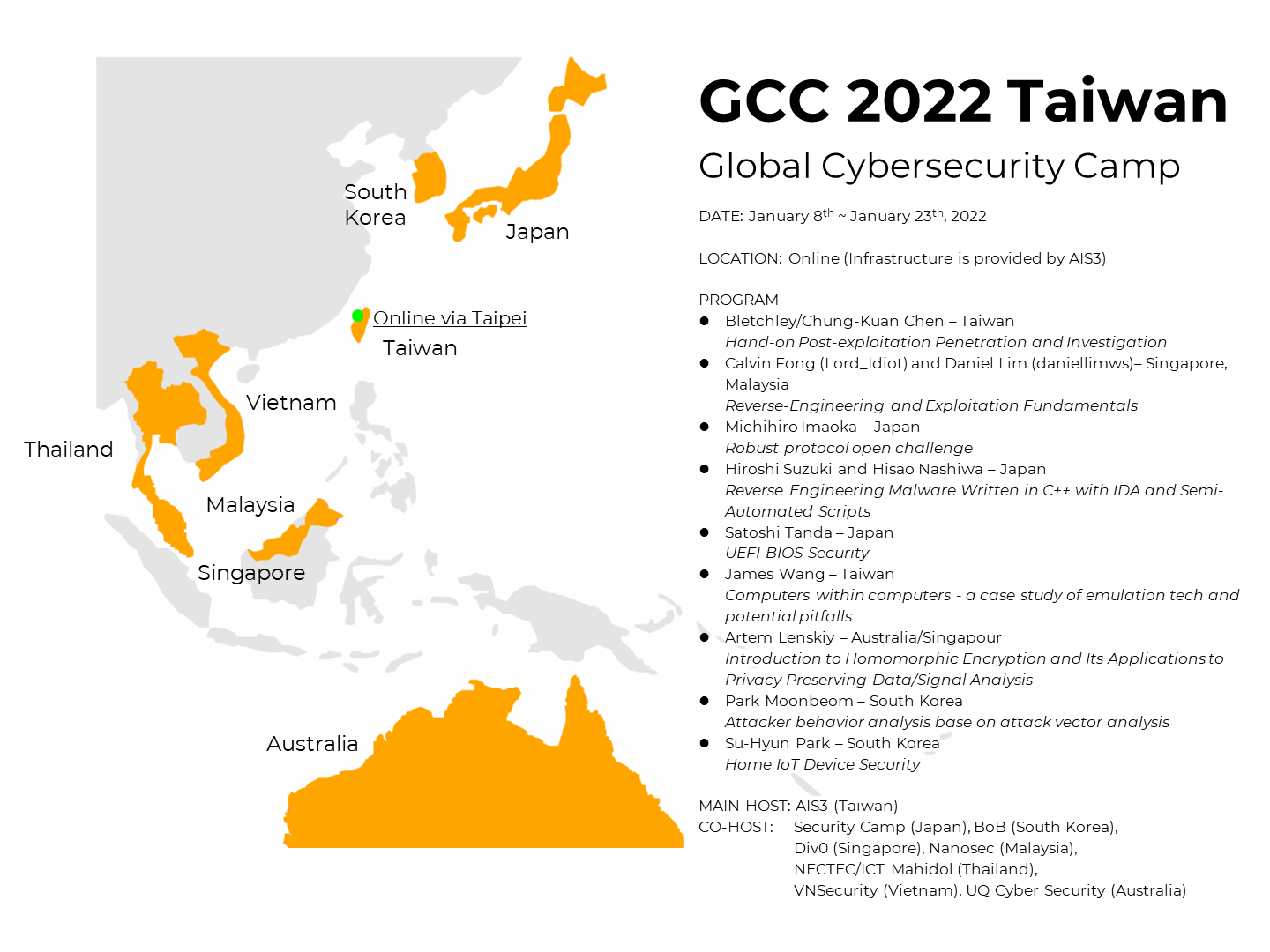
GCC 2022 Taiwan
Introduction
- Location: Online (Infrastructure is provided by AIS3)
- Days: 8th January ~ 23rd January, 2022
Every Saturday and/or Sunday during 9:00 AM to 7:00 PM (UTC+8) - Eight countries are participating (maximum 48 students)
- Pre-assignment of course will be held at Slack workspace
Mission of the GCC
Strengthen the security community across Asia and nurture future global leaders.
Annually, the best 48 students (maximum) from member countries gather in one of the participating countries for a week to exchange experience, forge a life-long friendship, and learn from the best cybersecurity professionals.
Non-commercial education programs and communities organize the program supported by industry leaders who care about the safe digitalization of the world.
Timetable of GCC 2022 Taiwan
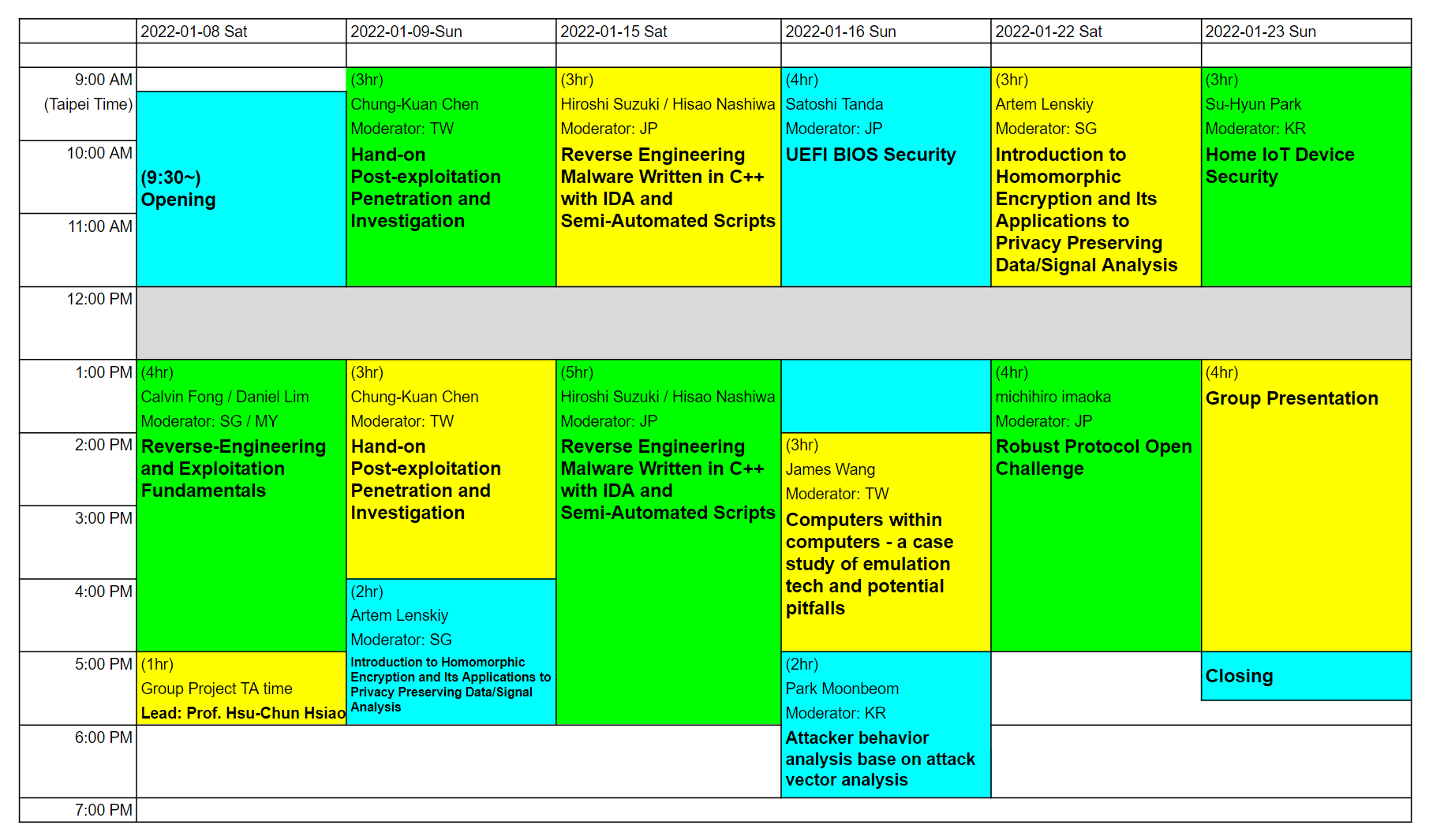
Update (2022-01-05):
Added time slot for group-work in 2022-01-08 Sat.
Information of each lecture
Hand-on Post-exploitation Penetration and Investigation
Abstract
Post-exploitation is the phase of intrusion after the adversary compromised the systems by a successful exploitation. Post-exploitation phase is critical for threat actors, but very often to be overlooked. Since the complicated IT infrastructure, exploitation and malware infection are unavoidable, thus tracking the post-exploitation activities become one main task for organization’s blue teams.Generally speaking, it contains activities from persistence, lateral movement, privilege escalation and command & control.
In this course, we start from the leaked tutorial of threat actors, e.g. Conti ransomware group. The tutorial can give us a glimpse about how threat actors do post-exploitation. Then we make hand-on practice of post exploitation techniques with the MITRE ATT&CK matrix as our map.
Next, one important environment - Active Directory (AD) is introduced. While most organizations apply Windows-based OS as their main system, AD which is the core of the domain network of Windows becomes the strategic location for adversary. Moreover, the complexity of the AD system makes it troublesome to configure secure.
In the end, we will both use endpoint and network threat hunting techniques to detect these post-exploitation activities that we conducted in the previous phase.
Trainer
Name: Bletchley/Chung-Kuan Chen
Bio :
Chung-Kuan Chen is currently a senior researcher in CyCraft, and responsible for organizing the research team, and Adjunct Assistant Professor in Soochow Uiniversity, Taiwan. He earned his PHD degree of Computer Science and Engineering from National Chiao-Tung University (NCTU). His research focuses on cyber attack and defense, machine learning, software vulnerability, malware and program analysis. He tries to utilize machine learning to assist malware analysis and threat hunting, and build automatic attack and defense systems. He has published several academic journal and conference papers, and has been involved in many large research projects from digital forensic, incident response to malware analysis. He also dedicates to security education. Founder of NCTU hacker research clubs, he trained students to participate in world-class security contests, and has experience of participating DEFCON CTF (2016 in HITCON Team and 2018 as coach in BFS team). He organized the BambooFox Team to join some bug bounty projects and discover some CVEs in COTS software and several vulnerabilities in campus websites. Besides, he has presented technical presentations in technique conferences, such as BlackHat, HITCON, CHITB, RootCon, CodeBlue, FIRST and VXCON. As an active member in Taiwan security community, he is the chairman of HITCON review committee as well as director of Association of Hacker In Taiwan, and member of CHROOT - the top private hacker group in Taiwan.
Reverse-Engineering and Exploitation Fundamentals
Abstract
EternalBlue, iPhone jailbreaks, game hacks. All these wonderful feats of hacking wizardry would not be possible without fundamental reverse-engineering and exploitation skillsets. However, such an interesting area of cybersecurity does not come without its downsides. The barriers to entry into this area are very high, and many have difficulty learning these skills. With our training, we cover the essential skills and knowledge required to power your journey into this wonderful domain.
Trainer
Name: Calvin Fong (Lord_Idiot) and Daniel Lim (daniellimws)
Bio:
Calvin
- Pwn2Own 2021 Participant
- Ex-intern @ STAR Labs
- Codegate Junior 2019, 2nd Place
- ACSC Singapore Representative
- GCC 2018 Alumni
Daniel
- Intern @ STAR Labs
- GEF Maintainer (https://github.com/hugsy/gef)
- President @ NUS Greyhats
- ACSC Malaysia Representative
Reverse Engineering Malware Written in C++ with IDA and Semi-Automated Scripts
Abstract
C++ is widely used in a variety of malware, such as RATs and banking Trojans, etc. Malware written in C++ is often object-oriented. Analyzing it requires knowledge and experience with classes and their inheritance, vtable, and basic strings, in addition to knowledge of analyzing malware written in C. In this course, attendees will learn how to quickly find and deal with such features.
In this course, we will use IDA Free for analysis. Although Ghidra, which is popular among CTF players these days, is useful for analyzing simple and/or small programs, and under certain conditions, it is still inferior to IDA in many aspects, such as processing speed, decompiler accuracy, and a variety of third-party scripts and plug-ins. IDA is still the de facto standard reverse engineering tool.
One of the trainers has developed and released a third party plug-in for IDA called CTO (Call Tree Overviewer). He will also explain how to use it to perform analysis more efficiently.
In this course, while learning how to use IDA, we will analyze actual malware written in C++, and aim to learn the techniques including the know-how. Afterwards, we will practice the techniques we have learned through CTF-style games, having fun, cooperating and competing with each other.
Trainer
Name: Hiroshi Suzuki and Hisao Nashiwa
Bio :
Hiroshi Suzuki is a malware analyst, a forensic investigator, an incident responder and a researcher, working for a Japanese ISP, Internet Initiative Japan Inc. He is a member of IIJ-SECT, which is the private CSIRT of his company. He is especially interested in targeted attacks, their RATs and their attack tools, such as PlugX, Mimikatz and so on. He has over 16 years dedicated to these areas. He has been a speaker and a trainer for international conferences such as Black Hat (USA, Europe, Asia and Japan), Virus Bulletin, and FIRST conference (Annual and TC) multiple times.
Hisao Nashiwa is a threat analyst, working for Internet Initiative Japan as a CSIRT member of the company. His main jobs include incident response, analyzing malware and analyzing network traffic. He has observed malicious activities for over ten years. He researches cyber crimes, He has eight years of experience and knowledge in analyzing malware. He has been a speaker and a trainer for international conferences such as Black Hat and FIRST (Annual and TC) multiple times.
UEFI BIOS Security
Abstract
This training offers in-depth knowledge of Unified Extensible Firmware Interface (UEFI) BIOS, its security threats, and countermeasures.
In recent years, firmware has become one of the common attack targets due to its lower visibility for defenders and lessor security levels, as indicated by the Microsoft report in 2021, revealing that the 80% of organizations experienced firmware attacks in the past 2 years. Among many types of firmware, UEFI BIOS is one of the most attractive targets because of its wide adoption as well as the high privilege level that even exceeds that of hypervisors and operating systems. In fact, real-world adversaries abused UEFI and exploited relevant vulnerabilities to install backdoors and establish persistency that remained undetected for years. Lojax(2018), MosaicRegressor(2020), and FinSpy(2021) are some of the recent examples.
Despite this emerging threat, the industry is yet to be better equipped. Does the security software detect exploitation, are the incident response teams able to consider and analyze attacks through UEFI, how many defenders can reverse engineer them? Even worse, how well the UEFI architecture and security mechanisms are understood in the first place?
This training will help students familiarize themselves with UEFI and different types of threats through hands-on exercises using real-world samples, followed by the 4-hour long lecture and discussions. This includes but not limited to code analysis of UEFI runtime driver used for game cheating, reverse engineering of Windows malware that infects UEFI and System Management Mode (SMM) vulnerabilities, along with relevant detection and protection technologies such as Boot Guard, Secure Boot, Trusted Platform Module (TPM) and CHIPSEC.
Trainer
Name: Satoshi Tanda
Bio :
Satoshi Tanda (@standa_t) is a system software engineer and a security researcher with over a decade of experience. His experience spans over the areas of UEFI- and Windows kernel-module programming and reverse engineering, vulnerability discovery and exploitation, malware analysis, virtualization technologies, and teaching them to professionals and school students. He works at CrowdStrike and analyzes UEFI security threats at scale and discovered multiple vulnerabilities in UEFI BIOS.
Computers within computers - a case study of emulation tech and potential pitfalls
Abstract
A large proportion of modern infrastructure relies on utilization of emulation technology such as virtual machines or instruction level interpreters. In this course, we will dive into unicorn engine, a relatively modest/flexible multi-architectural emulator unveil its internal mechanisms, as well as how implementation flaws might manifest in such environment.
Trainer
Name: James Wang
Bio :
Ml engineer at day, pwner at night. Read and paint in my free time.
Robust Protocol Open Challenge
Abstract
In general, cyber security tends to focus on protecting information devices and data from malicious attackers. In addition to this, securing communication from accidents and natural disasters is also an important task of cyber security. We have designed a contest to compete for skills to accomplish such tasks.
Trainer
Name: Michihiro Imaoka
Bio :
Michihiro Imaoka is a founder of Imaoca Engineering Office. He is also an FPGA developer, an embedded system developer, and a writer. He has been a Microsoft MVP since 2014 (Windows development), Security Camp lecturer since 2015, Security Camp producer since 2018, and a Sechack365 Trainer since 2020.2020-2021 Blackhat USA Arsenal presenter. https://www.facebook.com/imaoka.micihihiro @imaoca
Introduction to Homomorphic Encryption and Its Applications to Privacy Preserving Data/Signal Analysis
Abstract
Cryptography has been an integral part of Internet communications for many decades. However, with regard to processing received or sent data, it should be decrypted first. In this session, concepts of homomorphic encryption (HE) that allow for direct computation over encrypted data will be introduced. Recently, a number of practical HE schemes have been developed by Microsoft and other Tech Giants that in turn sped up the adaption of HE by cloud computing services. The session begins by providing the definition of homeomorphism that is supplemented by an example of an HE scheme that relies on the factorization difficulty of a number into its prime. Then we proceed to implementing a machine learning algorithm over encrypted data using CKKS scheme, the limitations of this scheme also presented. Further two practical applications of HE will be described: a trading algorithm that generates a buy or sell decision on encrypted data and a medical application that illustrates a potential use of HE in controlling insulin in diabetic patients.
Trainer
Name: Artem Lenskiy
Bio :
Artem Lenskiy received his PhD in Electrical Engineering from the University of Ulsan, South Korea with the funding by the Agency for Defense Development, and currently is finishing his second master’s degree in Applied Mathematics at Johns Hopkins. He has over 15 years of experience in data analysis, software development, and mathematical modelling. He consults government organisations, proprietary trading firms, and has delivered projects for the Department of Defence, the Department of Health and the Department of Industry Science Energy and Resources. Artem has published in numerous journals on homomorphic encryption, algorithmic trading, and machine learning, and given talks on these topics at Australian universities, IPAA ACT, and several private organisations. He has also taught over 15 computer science and math courses at the undergraduate and graduate levels. He is currently supervising over 10 graduate students at the ANU. In his spare time, he enjoys riding a bicycle, swimming, and math blogging.
Attacker behavior analysis base on attack vector analysis
Abstract
Analysis hacking technique to analyze the victim system hacked by the attacker, and analysis various logs on the victim system to reconstruct the attacker’s behavior.
Trainer
Name: Park Moonbeom
Bio :
I’m working in cyber security and incident response sector of South Korea as a general researcher and cyber investigation advisory member of the national investigation agency. Also I’m responsible for research on hacking methods, analyze hacking incident also, profiling the relationships. And I’m not only one of the leaders in Asia’s oldest underground hacker group, but also an instructor and mentor in the program(a.k.a BoB) to train ethical hackers in South Korea.
Home IoT Device Security
Abstract
There are a lot of home IoT (Internet of Things) devices at your home these days. Smartphones, tablets and smartwatches are very common. Smart TVs, fridges and even door locks and multiplugs are now connected to the Internet nowadays. I will discuss how securely these devices are communicating through the web.
Trainer
Name: Su-Hyun Park
Bio :
15+ years in cybersecurity arena. Developing network security products that protect systems from hacker attacks in network, IoT and cloud cyberspaces.