GCC 2023 Singapore
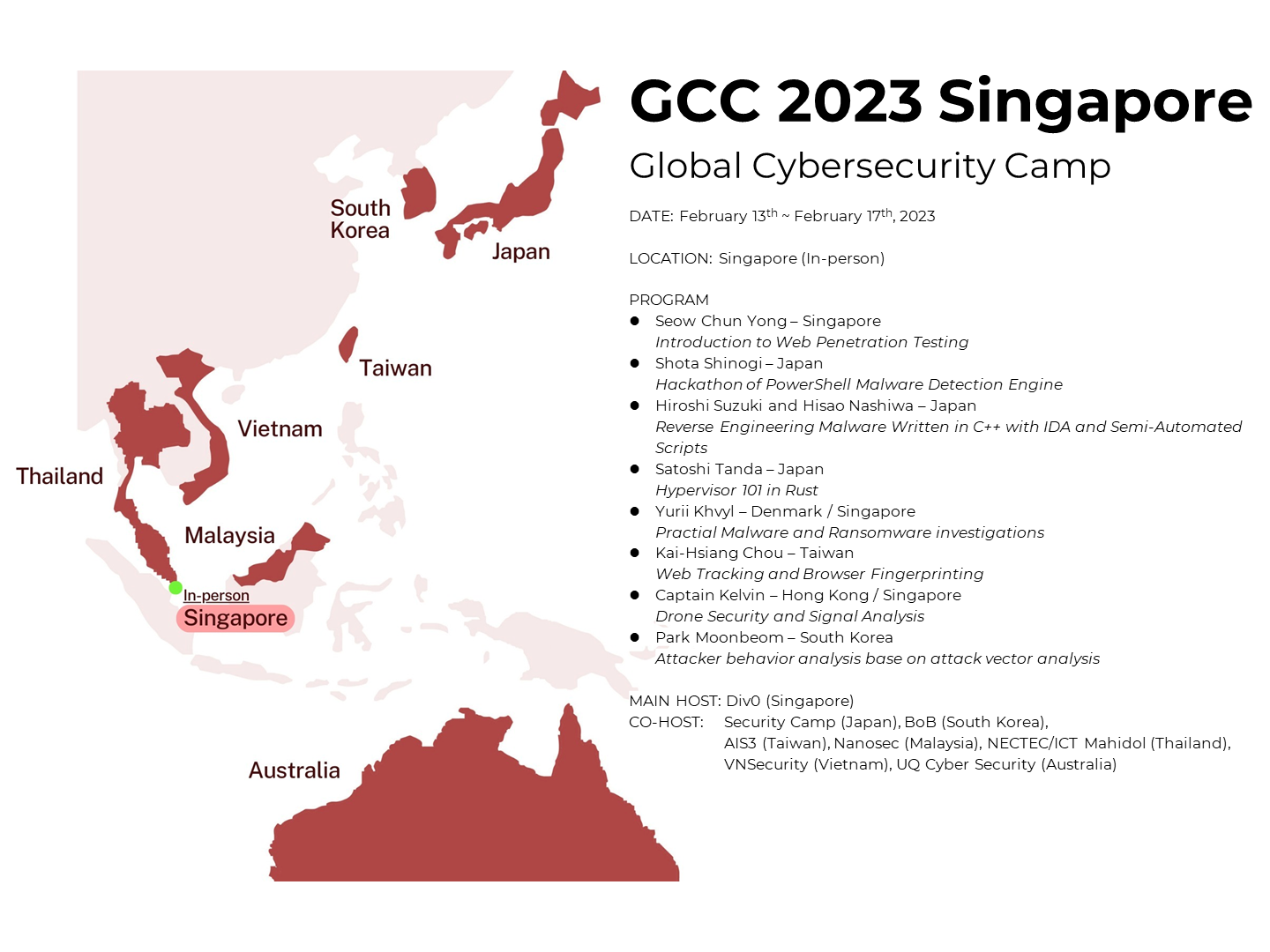
Introduction
- Location: Singapore
- Days: 13th February ~ 17th February, 2023
- Eight countries are participating (maximum 48 students)
Mission of the GCC
Strengthen the security community across Asia and nurture future global leaders.
Annually, the best 48 students (maximum) from member countries gather in one of the participating countries for a week to exchange experience, forge a life-long friendship, and learn from the best cybersecurity professionals.
Non-commercial education programs and communities organize the program supported by industry leaders who care about the safe digitalization of the world.
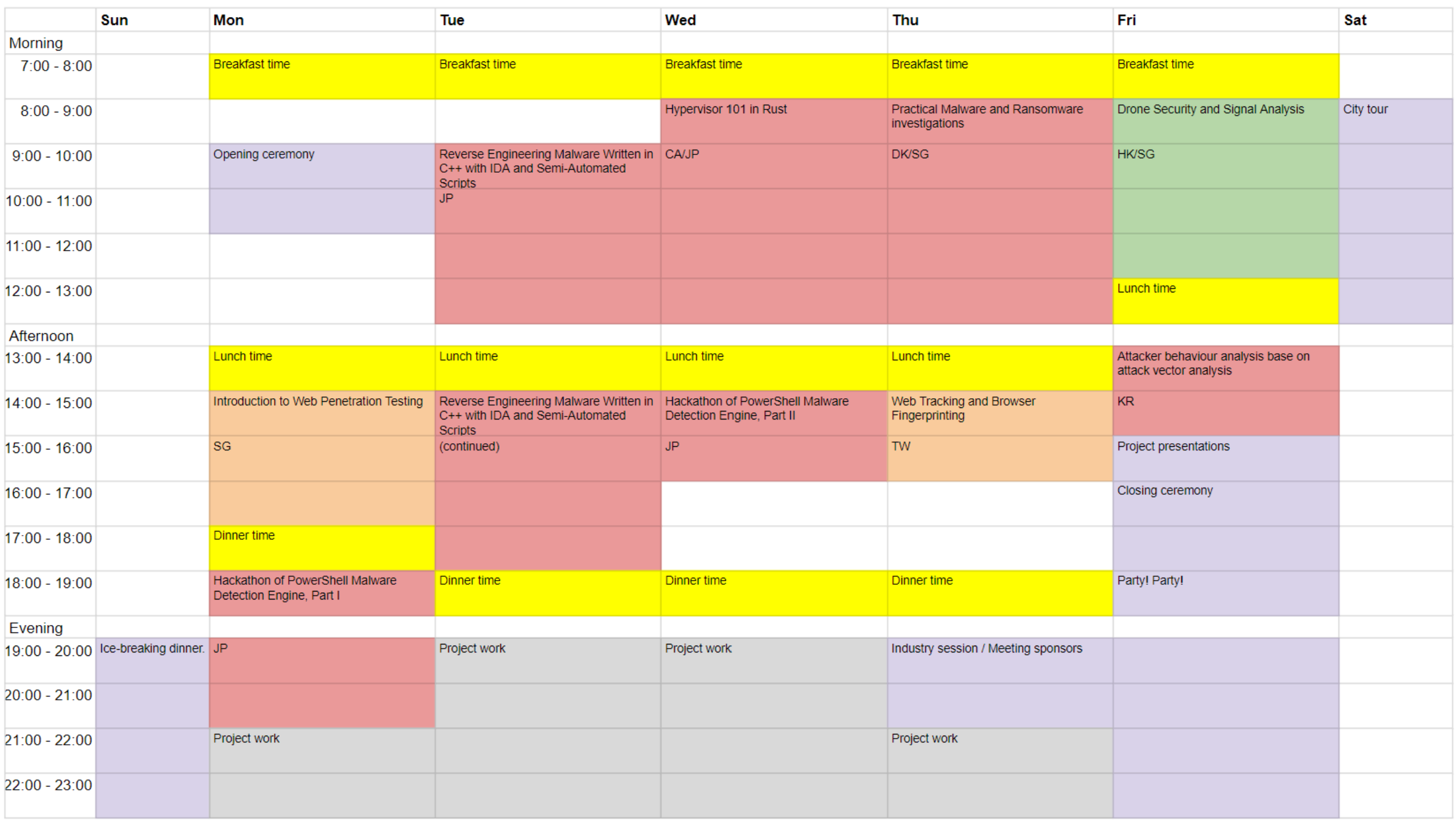
Timetable of GCC 2023 Singapore
Information of each lecture
Introduction to Web Penetration Testing
Trainer: Seow Chun Yong [SG]
Abstract
Learn about the basics of web penetration testing, how websites work, and how to get started using Burp Suite.
Trainer Bio(s)
Lead of Penetration Testing and Red Team
Hackathon of PowerShell Malware Detection Engine
Trainer: Shota Shinogi [JP]
Abstract
PowerShell based malware is everywhere. It is often executed from Office macro or shortcut(LNK) or exploit + shellcode. The functionality can vary but we observed the powershell script used as a stager to download or extract the next malware a lot, and sometimes as backdoor or ransomware. The attackers use the PowerShell because it is a default tools on Windows and the script can be run without touching the file system; file-less. And the most important part is that there are hundreds way to obfuscate the script to make the detection harder.
Microsoft is fighting against those malicious PowerShell with AMSI (AntiMalware Scan Interface) but the attackers always use bypass techniques.
The training will start with some lecture about basics of PowerShell and its obfuscation techniques. Then the attendess will split into small groups and get asked to write a detection engine using the PowerShell logging feature of Windows by Python. The attendees will start with considering the methodology to detect the malicious script. For example, it can be pattern match / black-listed API, symbols-alphanumeric frequency rates, or even AI based text detection engine. Any methodology will be welcomed as long as the attendees can build it. The last part of the training will be a competition, which detection engine is the best. Each group will bring their detection engine and we will measure the detection rate using malware samples.
Trainer Bio(s)
Shota Shinogi is a security researcher at Macnica (Japan), pentest tools author and CTF organizer. He is an expert in writting malware for Red Team purpose and to evade the detection from EDR, sandbox, IPS, antivirus and other security solutions. He has more than 10 years experience on the Cyber security industries, starting his carrier with HDD Encryption, NAC, IPS, WAF, Sandbox. He has spoken in several security/hacking conferences; Black Hat, DEF CON, BSides. He is also contributing for the education for the next generation security engineer through the Security Camp from 2015 consecutively in Japan.
Reverse Engineering Malware Written in C++ with IDA and Semi-Automated Scripts
Trainer: Hiroshi Suzuki / Hisao Nashiwa [JP]
Abstract
C++ is widely used in a variety of malware, such as RATs and banking Trojans, etc. Malware written in C++ is often object-oriented. Analyzing it requires knowledge and experience with classes and their inheritance, vtable, and basic strings, in addition to knowledge of analyzing malware written in C. In this course, attendees will learn how to quickly find and deal with such features.
In this course, we will use IDA Free for analysis. Although Ghidra, which is popular among CTF players these days, is useful for analyzing simple and/or small programs, and under certain conditions, it is still inferior to IDA in many aspects, such as processing speed, decompiler accuracy, and a variety of third-party scripts and plug-ins. IDA is still the de facto standard reverse engineering tool.
In this course, while learning how to use IDA, we will analyze actual malware written in C++, and aim to learn the techniques including the know-how. Afterwards, we will practice the techniques we have learned through CTF-style games, having fun, cooperating and competing with each other.
Trainer Bio(s)
Hiroshi Suzuki
Hiroshi Suzuki is a malware analyst, a forensic investigator, an incident responder and a researcher, working for a Japanese ISP, Internet Initiative Japan Inc. He is a member of IIJ-SECT, which is the private CSIRT of his company. He is especially interested in targeted attacks, their RATs and their attack tools, such as PlugX, Mimikatz and so on. He has over 17 years dedicated to these areas. He has been a speaker and a trainer for international conferences such as Black Hat (USA, Europe, Asia and Japan), Virus Bulletin, and FIRST conference (Annual and TC) multiple times.
Hisao Nashiwa
Hisao Nashiwa is a threat analyst, working for Internet Initiative Japan as a CSIRT member of the company. His main jobs include incident response, analyzing malware and analyzing network traffic. He has observed malicious activities for over ten years. He has nine years of experience and knowledge in analyzing malware. He has been a speaker and a trainer for international conferences such as Black Hat and FIRST (Annual and TC) multiple times.
Hypervisor 101 in Rust
Trainer: Satoshi Tanda [JP]
Abstract
In this class, we will learn the basics of hardware-assisted virtualization technologies on x86 through writing a custom hypervisor in Rust for kernel-code fuzzing.
Hardware-assisted virtualization such as Intel VT-x and AMD-V is the technology that enables today’s many workloads, including cloud computing, isolated software development and validation, and security research. While the understanding of “how it works” is essential for auditing such solutions as well as using the technology for creative purposes, gaining knowledge and experience in this domain is often challenging due to its low-level nature.
Given that, this course will offer the basic knowledge of how hypervisors realize the concept of “VMs”, and as an application of the concept, hands-on experiences in implementing the snapshot-based fuzzer that runs a target as a VM. The hands-on exercises include learning VMCS/VMBC, EPT/NTP, exception interception as well as debugging of CPU itself using Bochs.
With knowledge acquired by this course, the most successful students would discover 0-day vulnerabilities in non-user-mode software such as kernel and UEFI modules by extending their hypervisors or effectively using similar fuzzers such as WTF with the understanding of underneath technology.
Trainer Bio(s)
Satoshi Tanda (@standa_t) is a system software engineer and a security researcher with over a decade of experience. His experience spans the areas of virtualization technologies, UEFI- and Windows kernel-module programming and reverse-engineering, vulnerability discovery and exploitation, malware analysis, and teaching them to professionals and school students. He has taught hypervisor development for well over 100 working professionals. He works at CrowdStrike and develops Windows security software in Rust and C++.
Practial Malware and Ransomware investigations
Trainer: Yurii Khvyl [DK/SG]
Abstract
First Part: Practial Malware investigations
From capturing sample, different way of analisys(sandbox, protocol, reverse engineering), simulating protocol and monitoring, investigating infrastructure, making shutdown.
Will be overviewed different practical cases , where author was involved from begining till the shutdown.
Second Part: Ransomware Attack Analysis and Mitigation
Review of Ransomware technics from first infection vector, and then their different technics to get network access, and used tools. Will be reviewd practical examples of ransomware attacks, and different ways to recover company. (finding weeknes of encryptions algorithm, weeknes in encryption program, and also different ways of ransom payment negotiation).
Overview of internal structure of ransomware gangs, and they tools and technics.
Trainer Bio(s)
Have +15 years of expirience in Security Industry. Worked in CSIS Security Group, Denmark for more than 10 years on position Senior Malware Analyst. Participated in different security conferences, like DCC, Frist, AVAR, CARO.
Web Tracking and Browser Fingerprinting
Trainer: Kai-Hsiang Chou [TW]
Abstract
Web tracking is the technique of assigning each user a distinct identifier so that future visits from the same users, whether or not to the same websites, may be recognized and linked. While web tracking techniques have some legitimate usages, they are often used in privacy-intrusive ways, such as profiling and ad targeting. In the early days, many advertisers and website owners relied on stateful tracking techniques. Recently, many have adopted stateless techniques, especially browser fingerprinting, due to their effectiveness and difficulties in blocking them. By running a script to collect browser-specific data, one may identify and track the users without storing any stateful identifiers. This training will introduce several common and novel web tracking techniques, including stateful tracking and browser fingerprinting, their mitigations, and open challenges. We will also discuss some progress in privacy-preserving web tracking.
Trainer Bio(s)
Kai-Hsiang Chou is an undergraduate interesting in web security. He was the lecturer at HITCON 101 hosted at HITCON 2018 and HITCON workshop hosted at HITCON 2022. Kai-Hsiang Chou is also known as Allen Chou.
Drone Security and Signal Analysis
Trainer: Captain Kelvin [HK/SG]
Abstract
Advancements in UAV technology are opening new opportunities and applications in various fields of life. However, these advancements are also causing new challenges in terms of security, adaptability, and consistency. Especially the small drones are even suffering from architectural issues and the definition of security and safety issues.
Trainer Bio(s)
Captain is an independent security researcher. He focus on hardware analysis and forensics research. He was the first and the only one Asian who was leading a group of white-hat hackers to held an in-depth and hands-on hardware hacking village in DEFCON. He was also a frequent speaker and trainer in different top-level security and forensics conferences.
Attacker behavior analysis base on attack vector analysis
Trainer: Park Moonbeom [KR]
Abstract
Analysis hacking technique to analyze the victim system hacked by the attacker, and analysis various logs on the victim system to reconstruct the attacker’s behavior.
Trainer Bio(s)
General Researcher