GCC 2024 Thailand
Introduction
- Location: Thailand
- Days: 19th February ~ 24th February, 2024
- Ten countries are participating (maximum 50 students)
Mission of the GCC
Strengthen the security community across Asia and nurture future global leaders.
Annually, the best 50 students (maximum) from member countries gather in one of the participating countries for a week to exchange experience, forge a life-long friendship, and learn from the best cybersecurity professionals.
Non-commercial education programs and communities organize the program supported by industry leaders who care about the safe digitalization of the world.
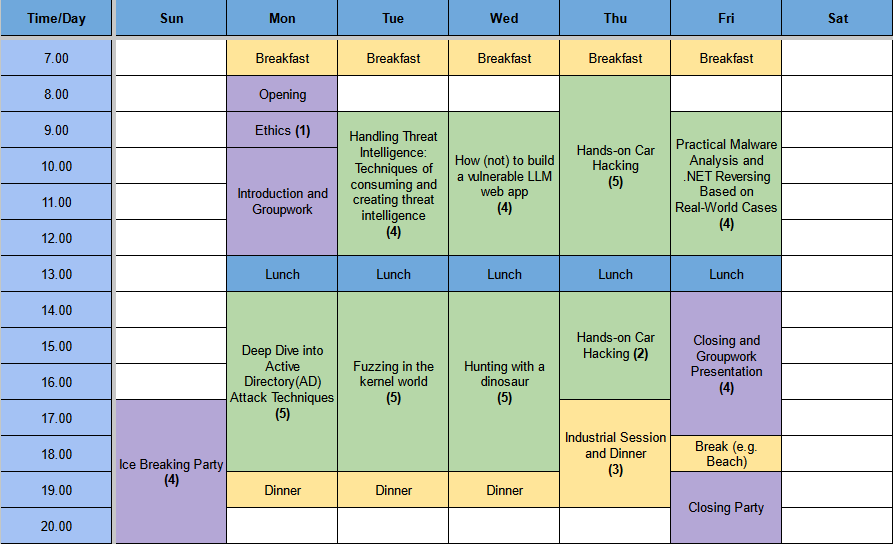
Timetable of GCC 2024 Thailand
Information of each lecture
Deep Dive into Active Directory(AD) Attack Techniques
Trainer: Mars Cheng [TW]
Abstract
For either On-Premises, Hybrid, or Azure environments, Microsoft Active Directory (AD) is widely used by enterprises as a backbone for identity and access management. AD is recognized by adversaries for providing access to a company’s crown jewels. Although AD has critical functionalities for enterprise operation, attackers can abuse these mechanisms provided by AD services to compromise an enterprise network to achieve their operations.
In this training course, we will deep dive into On-Premises exploring different kinds of AD services and technologies. We will cover various AD attack techniques by abusing the underlying mechanisms. This course is expected to be lab-intensive with over 5 hands-on practices. For each training lab, there will be an in-depth discussion as a core concept to enable the student to understand the theoretical background and effectively implement an attack technique.
Trainer Bio(s)
Mars Cheng (@marscheng_) is a threat research manager of TXOne Networks PSIRT and threat research team, responsible for coordinating product security and threat research, and is the executive director of the Association of Hackers in Taiwan. Mars blends a background and experience in both ICS/SCADA and enterprise cybersecurity systems. Mars has directly contributed to more than ten CVE-IDs, and has had work published in three Science Citation Index (SCI) applied cryptography journals. Before joining TXOne, Cheng was a security engineer at the Taiwan National Center for Cyber Security Technology (NCCST). Mars is a frequent speaker and trainer at several international cyber security conferences such as Black Hat USA/Europe/MEA, RSA Conference, DEFCON, SecTor, FIRST, Troopers, CODEBLUE, HITB, ICS Cyber Security Conference Asia and USA, ROOTCON, HITCON, SINCON, CYBERSEC, and CLOUDSEC. Mars was the general coordinator of HITCON (Hacks in Taiwan Conference) PEACE 2022, HITCON 2021, and vice general coordinator of HITCON 2020.
How (not) to build a vulnerable LLM web app
Trainer: Shota Shinogi [JP]
Abstract
Since OpenAI released the ChatGPT API (to be more specific; Completion API), the era of LLM integrated system has come. Many companies build chatbot, or more complex web applications, to guide the user, or to perform some business operation, identifiing malware. Then a new hacking technique “Prompt Injection” was born. The session will cover how to build a system with LLM, then the hacking technique related to LLM; jailbreak to bypass the safeguard of LLM, prompt leaking to steal the prompt, prompt injection to manipulate the LLM result, and more attack method to finally compromise the whole LLM integrated web app.
Trainer Bio(s)
Shota Shinogi is a security researcher at Macnica, pentest tools author and CTF organizer. He is an expert in writting malware for Red Team purpose and to evade the detection from EDR, sandbox, IPS, antivirus and other security solutions. He built multiple LLM projects to research on LLM integegrated system vulnerabilities. He has more than 10 years experience on the Cyber security industries, starting his carrier with HDD Encryption, NAC, IPS, WAF, Sandbox solutions and corresponding hacking technologies. He has spoken in several security/hacking conferences; Black Hat, DEF CON, BSides.
Handling Threat Intelligence: Techniques of consuming and creating threat intelligence
Trainer: Tomohisa Ishikawa [JP]
Abstract
To prevent advanced threat actors from compromising systems and mitigate similar attacks, it is crucial to employ threat intelligence. This involves the collection, analysis, and dissemination of diverse information regarding threat actors and their Tactics, Techniques, and Procedures (TTPs). Effective prevention and detection rely heavily on this practice. Additionally, by sharing analyzed and generated threat intelligence both within and beyond the organization, we can enhance early warning mechanisms for the industry and cybersecurity communities.
When discussing the “analysis of attack”, security engineers typically think of techniques such as malware analysis, vulnerability assessment, and forensics. However, a fundamental question arises: How can we effectively utilize the outcomes of technical analysis to enhance prevention and detection efforts?
In this lecture, we will explore three key areas. Firstly, we will delve into the foundational principles of threat intelligence theory, covering various concepts such as the types of intelligence, the threat intelligence cycle, and attribution. Secondly, we will focus on analysis techniques and the practical application of threat intelligence. Drawing from information obtained through activities like malware analysis and forensic analysis, we will learn how to leverage frameworks like MITRE ATT&CK to comprehend TTPs. We will also explore how to apply this knowledge to threat hunting, purple teaming, and discussions regarding countermeasures. In the third part of the lecture, we will explore the process of translating this acquired threat intelligence into actionable prevention and detection measures. This will involve learning about the creation of Indicators of Compromise (IOCs) using tools such as YARA and SIGMA.
Trainer Bio(s)
Tomohisa works as the Lead Cyber Security Architect at a global insurance company. In this role, he has been involved in a wide range of security projects and operations, encompassing global security strategy, security architecture, threat intelligence analysis, and digital forensics and incident response (DFIR). His extensive background also includes experience in red teaming, forensics, and security training. Tomohisa holds a Doctor of Engineering degree and is certified in various cybersecurity domains, including CISSP, CSSLP, CISA, CISM, CDPSE, CFE, PMP, and several GIAC certifications (GWAPT, GPEN, GDAT, GSNA), among others.
Furthermore, Tomohisa has made significant contributions to the cybersecurity community. He is an accomplished speaker, serves as a member of the GIAC Advisory Board, participates in national IT Exam Committees, and works as Lead QA/QC for SANS e-learning. He is also a professional translator and author. Tomohisa has delivered talks at renowned conferences such as SANSFIRE (in 2011 and 2012), DEFCON 24 SE Village, FIRSTCON23, Security Camp 2023, and various other security conferences. Additionally, he has authored a book on threat intelligence in Japanese and has translated four DFIR books and one API security book from O’Reilly Japan.
Fuzzing in the kernel world
Trainer: Yi-Han Wang [TW]
Abstract
Fuzzing is an important tool for finding out security bugs automatically. Today, the lecturer will primarily focus on system-level fuzzing, as implementation bugs at this level can cause severe and disastrous consequences. The course will begin with a thorough overview of general fuzzers, followed by an introduction to virtualization and system-level fuzzers. Throughout the course, the lecture will explain the concept and motivate participants to conduct their own tests using fuzzers. The aim is for everyone to gain a comprehensive understanding of fuzzing technology and its practical applications.
Trainer Bio(s)
- Graduated from the Department of Computer Science and Information Engineering at National Taiwan University
- A member of Balsn, a talented CTF team in Taiwan
- A member of the HITCON GIRLS binary team
- A software engineer at Google
Hunting with a dinosaur
Trainer: Andreas van Leeuwen Flamino [NL]
Abstract
In this training students will learn how to rapidly become better at digital forensics, threat hunting and incident response. We will explore how it’s easier to increase your understanding and experience 10 times than 2 times, if you take a different approach. By focusing on building a deep fundamental understanding of core operating system artifacts, and then learning how to combine them, you can improve more in a shorter amount of time.
Trainer Bio(s)
Andreas is a seasoned cyber security professional, with over two decades of experience across red and blue teams.
In the late 1990s he started his security career as Linux and UNIX systems administrator. He continued as a red teamer in the early 2000s. Since then, he delivered dozens of security consultancy projects across diverse industry verticals. They include banking, oil & gas, government, law enforcement, defense, telco, aviation, and manufacturing.
In the last six years, he sharpened his Threat Hunting, Incident Response and Digital Forensics skillsets. He worked many high-profile Incident Response projects for the UAE government. In one project he was the resident DFIR Lead at EXPO2020. From 2019 to 2023, he grew to become a top performer in the largest IR team in the UAE. He currently heads up the Cyber Intelligence Center at an Oil & Gas company in Dubai. In his free time he offers his expertise as IR practitioner and trainer.
Hands-on Car Hacking
Trainer: Kamel Ghali [JP]
Abstract
This training introduces participants to the world of car hacking and automotive cybersecurity. Participants will learn about the nuances of security in the automotive industry and about technologies specific to vehicle security. Hands-on training modules are also prepared, giving the attendees the opportunity to use real automotive technology and tools used in the automotive security industry. Participants will get hands-on training using CAN bus and Bluetooth security, two of the most commonly found technologies in modern vehicles.
Trainer Bio(s)
Kamel is a veteran of the automotive cybersecurity community, having spent over 3 years as an expert car hacker, technical trainer, and contributor to worldwide industry-focused communities such as the SAE, ASRG, and the Car Hacking Village. His particular areas of focus within vehicle security are Bluetooth, RF, and in-vehicle networks. Outside the garage, Kamel is an amateur chef, ukulele player, and fighting game enthusiast.
Practical Malware Analysis and .NET Reversing Based on Real-World Cases
Trainer: Wei-Chieh Chao [TW] / Yi-Hsien Chen [TW]
Abstract
This training course covers practical malware analysis and .NET reversing, providing participants with a comprehensive understanding of different types of malware and their capabilities, as well as the common behavior and techniques used by malware. We will explore both dynamic and static analysis using tools such as x64dbg, Ghidra. The training emphasizes hands-on experience with real-world cases, including ransomware analysis and fileless backdoors. The course will also focus on .NET reversing and background knowledge of .NET Framework, including the Common Language Runtime (CLR) and the Common Intermediate Language (CIL). We will also look at .NET packers internal and unpackers like General packer and JITHook, and analyzing real-world cases. By the end of the course, participants will have gained a practical understanding of malware analysis and .NET reversing, as well as the skills and knowledge needed to analyze real-world cases.
Trainer Bio(s)
Wei-Chieh Chao
Wei-Chieh Chao is a security researcher of the Research Team of CyCraft. He focuses on research on Sandbox Technology and Malware Analysis. He graduated from National Taiwan University with master degree in Cyber Security. He was a speaker of HITCON, CodeBlue, IEEE DSC, and SECCON. In addition, he is also a member of the BambooFox CTF team at NCTU and has participated in several CTFs, and won 12th, 2nd in DEFCON 26, 27 with BFS, BFKinesiS CTF team. He also completed the Flareon9 reverse engineering challenge in 2022.
Yi-Hsien Chen
Yi-Hsien Chen earned his B.S. degree in Computer Science at National Chiao Tung University (NCTU) and is currently a Ph.D. candidate in the Department of Electrical Engineering at National Taiwan University (NTU), a research assistant in the Department of Computer Science at National Yang Ming Chiao Tung University (NYCU), and a security researcher for the CyCraft research team. His research focuses on automatic malware analysis techniques and various cybersecurity topics. He utilizes symbolic execution, machine learning, and other techniques to improve malware analysis speed. His work has been published in IEEE TIFS, DSC, and ACM ASIACCS. He has also spoken at HITB CyberWeek, AVTokyo, HITCON, SECCON, and CODE BLUE. Additionally, he was a member of the BambooFox CTF team from NYCU, has participated in several CTFs, and has won 12th and 2nd place in DEFCON 26 and 27, respectively, with BFS and BFKinesiS CTF teams.
Member Organizations
- Japan (Security Camp Committee)
- Singapore (Division Zero)
- South Korea (KITRI BoB Programme)
- Taiwan (Advanced Information Security Summer School)
- Malaysia (SherpaSec)
- Thailand (2600 Thailand)
- Vietnam (VNSEC)
- Australia (UQ Cyber Security)
- Indonesia (InfraDigital Foundation)
- India (Amrita Vishwa Vidyapeetham)